Issues around algorithm transparency and control over personal data have led to the rise of a concept known as “Self-Sovereign Identity”, or “SSI.”
One’s self-sovereign identity is neither dependent on nor subject to any other power or state. Self-sovereignty suggests that you are in control of your data and of how you self-identify; that you are in control over who you are, rather than some government agency, social network, corporation, or other external authority – that individuals control their personal data, digital identities and credentials.
What Is Meant By “Self-Sovereign Identity”?
A self-sovereign identity puts the user at the center of control. As a relatively new concept there are several descriptions of SSI worth considering:
– “Self-sovereign identity references every individual human identity as the origin of source authority,” and “a self-sovereign identity is the root of all participation as a valued social being within human societies of any type.” – moxytongue, Self-Sovereign Identity
– “Self-sovereign identity isn’t about administrative systems. It’s about you and me and how we selectively disclose personal information to others on a need-to-know basis, and being able to do that at scale.” – Doc Searls, Self-Sovereign Identity
– Self-sovereign identity has important business, legal and social dimensions. At one level, self-sovereign identity is a set of principles about how identity and personal data control should work across digital networks. At another level, self-sovereign identity is a set of technologies that build on core concepts in identity management, distributed computing, blockchain or distributed ledger technology, and cryptography.” – Alex Preukschat, Self-Sovereign Identity
What Are The Essentials Of Self-Sovereign Identity?
Regardless of the “self-sovereign identity” definition we prefer, all approaches indicate that the user must be first, not a third party or other outside authority. Aside from user-centric identity management, though, what are the other essentials required in achieving a system for self-sovereign identity?
This list of sovereign digital identity essentials is aggregated from The Laws of Identity, The Path to Self-Sovereign Identity, The Value of Our Digital Identity, Identity System Essentials, and Frank H. McCourt’s Our Biggest Fight:
Consent, User Control
Technical identity systems must only reveal information identifying a user with the user’s consent. Entities must be able to control their identities, they should always be able to refer, update or hide it. Entities should have direct access to their own identity and all related data. All data must be visible and accessible without gatekeepers.
Consistent Experience Across Contexts
The unifying identity metasystem must guarantee its users a simple, consistent experience while enabling separation of contexts through multiple operators and technologies.
Decentralized Storage
The information is distributed across a vast array of autonomous computers with no central entity in charge.
Digital Property Rights
You own whatever digital content you create, you own your social graph, and you own the right to monetize it.
Directed Identity
A universal identity system must support both “omni-directional” identifiers for use by public entities and “unidirectional” identifiers for use by private entities, thus facilitating discovery while preventing unnecessary release of correlation handles. “Another guiding principle of the [self-sovereign] identity system is that entities should own their identities, that is, have control over their own identity graphs. An entity is a sovereign source of identity when that entity is in control of its own identity graph including the creation, modification, storage, distribution, disclosure, and destruction of the associated identifiers and attributes.” – Samuel M. Smith, Identity System Essentials. Control over digital identifiers and attributes are a must for achieving a sovereign digital identity.
The connections between entities, identities, and attributes/identifiers are illustrated in the image below:
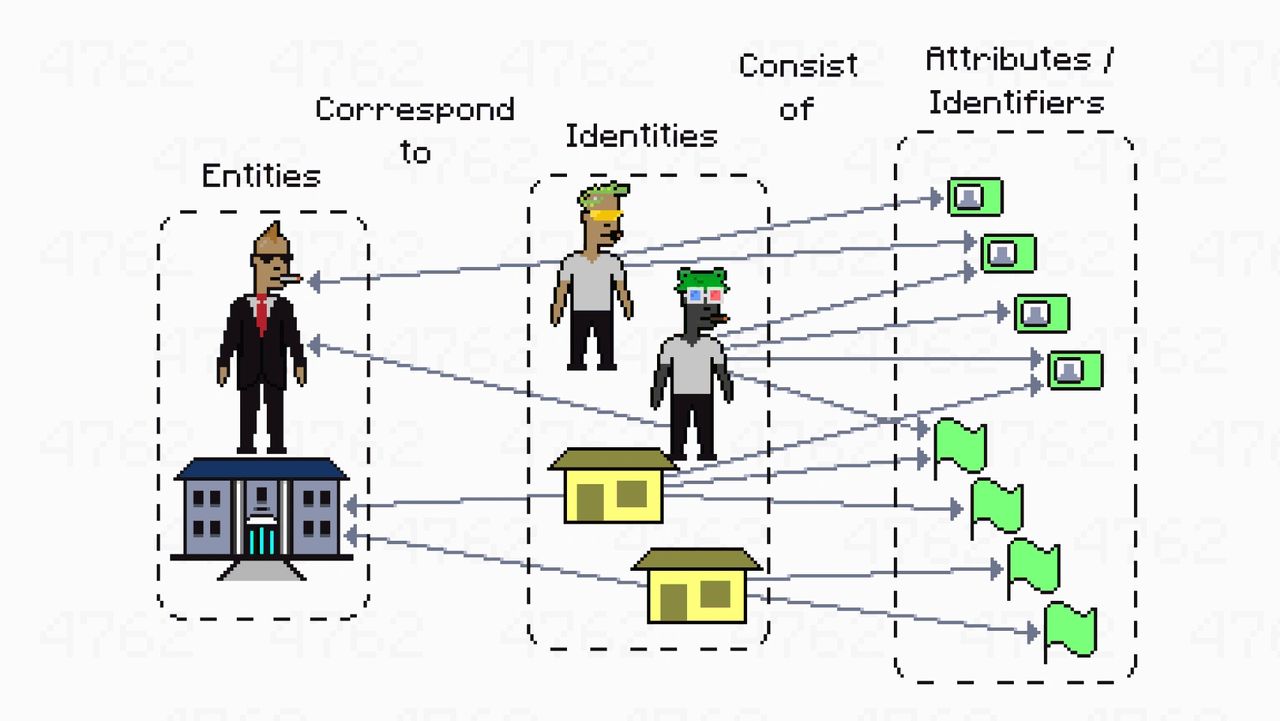
Human Integration
The universal identity metasystem must define the human user to be a component of the distributed system integrated through unambiguous human-machine communication mechanisms offering protection against identity attacks.
Interoperability, Pluralism Of Operators And Technologies
A universal identity system must channel and enable the inter-working of multiple identity technologies run by multiple identity providers. Identities should be as widely usable as possible. The system should be made modular.
Justifiable Parties
Digital identity systems must be designed so the disclosure of identifying information is limited to parties having a necessary and justifiable place in a given identity relationship.
Minimal Disclosure For A Constrained Use
The solution that discloses the least amount of identifying information and best limits its use is the most stable long-term solution. Disclosure of claims must be minimized.
Opt In, Not Opt Out
You choose when to signal your interest in something, who sees your content and connects with you, and what goes into your news feeds. You set the rules by which your data can be used.
Portability
All information about identities must be transportable. The identity must not be held by a singular third party. You can move your social graph data wherever you like, whenever you like. There are no more “walled gardens.”
Protection
The right of entities must be protected, when there is a conflict between the needs of the network and the right of entities, the priority should be the latter.
The Right To Be Forgotten
This has a small but consistently positive impact on the willingness of individuals to share private data.
Transparency
The system and its logic must be transparent in how they function, how they are managed and how they are kept up to date. The system should be made open-source to create the possibility for each entity to connect themselves.
Final Thoughts
Self-sovereign identity represents a fundamental shift in how we think about digital identity – from something managed for us to something we actively control. As we navigate an increasingly digital world where our personal data has become a valuable commodity, the principles of SSI offer a compelling vision for reclaiming agency over our digital selves.
The convergence of technological advances in cryptography, distributed systems, and blockchain with growing awareness of data privacy issues has created a unique moment for SSI to move from concept to reality. However, the true test of self-sovereign identity will not be in its technical elegance but in its practical adoption and ability to serve diverse communities with varying levels of technical expertise.
The essentials outlined here – from user control and consent to portability and the right to be forgotten – paint a picture of a more equitable digital future. Yet implementing these principles at scale requires not just technological innovation but also regulatory frameworks, business model shifts, and perhaps most importantly, a cultural change in how we value and protect digital identity.
As we stand at this crossroads between centralized identity systems and self-sovereign alternatives, the choices we make today will shape how future generations experience digital identity. The promise of SSI is not just about better technology – it’s about preserving human dignity and autonomy in the digital age. Whether we achieve this vision will depend on our collective commitment to putting individuals, not institutions, at the center of identity management.
The journey toward self-sovereign identity is just beginning, but the destination – a world where we truly own and control our digital selves – is worth pursuing.
Thanks for reading!
